We are excited to announce the General Availability of the world’s first security vulnerability scanner for EC2 Mac AMIs. EC2 Mac AMI Scan scans Intel and Apple Silicon macOS EC2 AMIs, detects security vulnerabilities in third-party packages, dependencies, and libraries, and generates formatted and human-readable reports. It’s like the container registry scanner but for your macOS AMI library.
When AWS announced the availability of macOS instances in late 2020, it was clear that iOS development teams would finally have access to Linux-like scalable and agile CI infrastructure. Now, as iOS development teams plan the migration of their iOS CI to AWS EC2 Mac infrastructure, security is at the top of their minds.
Working with the EC2 Mac instance is similar to working with a Linux instance on AWS, except that each EC2 Mac Instance runs on a single dedicated Mac host(mac mini Intel i7 or M1 mac mini). AWS security features like VPC, security groups, and IAM roles can be configured on EC2 Mac instances to secure the iOS CI environment.
One area that is exposed is the management of the guest operating system and the software deployed to the guest operating system. Mac machines that build, test, and deploy iOS apps can have many third-party dependencies, libraries, and packages like brew, pip, node, Cocoapods, npm, ruby, rust, Fastlane, Facebook snapshot testing library, xcodeapps, fabric, applyzer, transporter installed inside them. Any security vulnerability in the third-party dependencies, libraries, and packages can expose the build system and its assets to threat actors. A recent example is a zero-day exploit against the Log4J2 library, where it can allow an attacker to execute the code remotely, which has been reported with CVE-2021-44228 and CVE-2021-45046 against the log4j-core jar.
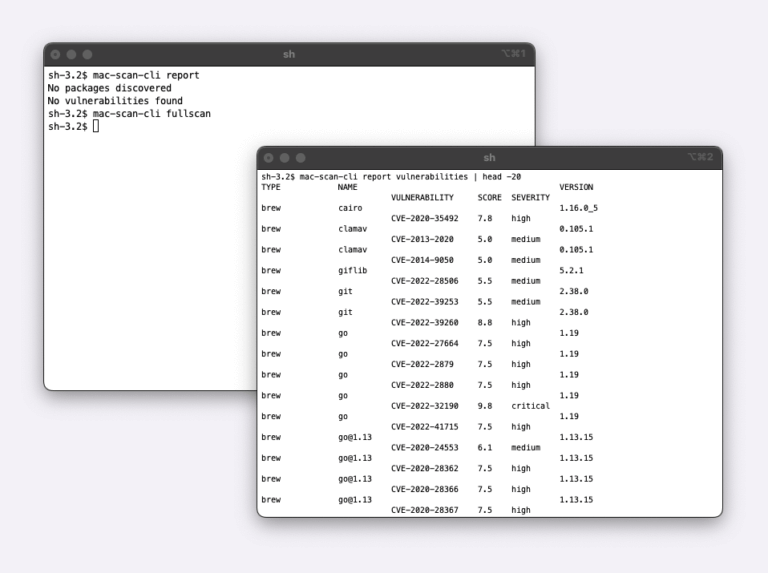
This is where the EC2 Mac AMI Scan fits in. EC2 Mac AMI Scan is the world’s first scanner tool to catalog all third-party packages installed in AWS EC2 Mac AMI and scan those for security vulnerabilities without needing to start an instance. EC2 Mac AMI Scan uses the NVD database to search for reported vulnerabilities. EC2 Mac Users can now scan continuously the EC2 Mac AMI used to create Mac instances for iOS CI.
AMI Scan runs on a small AWS Linux instance, mounts the target Mac AMI file system, and scans it for security vulnerabilities. DevOps can use the CLI interface of the EC2 Mac AMI Scan tool to integrate the Mac AMI scanning step into their existing packer-based AMI creation workflow and also set up a pipeline to scan existing AMIs for newly discovered vulnerabilities continuously.
Here is an example of a scan against an open source firefox-iOS project build environment AMI, which was built using amzn-ec2-macos-12.4-20220524-080745 AMI.
Step 1 – We took the amzn-ec2-macos-12.4-20220524-080745 AMI, started an ec2-mac instance from it, and created the firefox-iOS project build environment as per the instructions.
Step 2 – Then, we created the firefox-ios-mac-ami from step 1 and ran the scan tool against it to only show critical vulnerabilities.
[ec2-user@ip-172-31-50-40 ~]$ sudo ./ec2-mac-ami-scan_v1.0.0_linux_amd64 -i --min-severity critical ami-0a0fefafb17c54acd
✔ Vulnerability DB Update [completed]
✔ Attaching an AMI [attached vol-02622bc94272405e7]
✔ Cataloged packages [2323 packages]
✔ Indexed Data Volume
✔ Detaching an AMI [detached vol-02622bc94272405e7]
✔ Analyzed packages [110 vulnerabilities]
TYPE NAME VERSION VULNERABILITY SCORE SEVERITY
brew [email protected] 1.1.1o CVE-2022-2068 10.0 critical
brew [email protected] 3.9.13_3 CVE-2015-20107 10.0 critical
gem artifactory 3.0.15 CVE-2016-10036 9.8 critical
gem artifactory 3.0.15 CVE-2016-6501 9.8 critical
gem artifactory 3.0.15 CVE-2019-17444 9.8 critical
gem bundler 1.17.2 CVE-2020-36327 9.3 critical
gem bundler 1.17.2 CVE-2021-43809 9.3 critical
gem cocoapods-downloader 1.2.2 CVE-2022-21223 9.8 critical
gem cocoapods-downloader 1.2.2 CVE-2022-24440 9.8 critical
gem cocoapods-downloader 1.5.1 CVE-2022-21223 9.8 critical
gem cocoapods-downloader 1.5.1 CVE-2022-24440 9.8 critical
gem jmespath 1.4.0 CVE-2022-32511 9.8 critical
gem redis 3.2.1 CVE-2016-8339 9.8 critical
gem redis 3.2.1 CVE-2018-11218 9.8 critical
gem redis 3.2.1 CVE-2018-11219 9.8 critical
gem sync 0.5.0 CVE-2018-6892 9.8 critical
java-archive com.apple.transporter.log4j2 1.1.4 CVE-2019-17571 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-14379 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-14540 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-14892 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-14893 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-16335 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-16942 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-16943 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-17267 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-17531 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2019-20330 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2020-8840 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2020-9546 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2020-9547 9.8 critical
java-archive com.fasterxml.jackson.core.jackson-databind 2.9.8 CVE-2020-9548 9.8 critical
java-archive com.googlecode.plist.dd-plist 1.21.0 CVE-2022-22912 9.8 critical
java-archive dd-plist 1.21 CVE-2022-22912 9.8 critical
macos-app python 3.8.9 CVE-2015-20107 10.0 critical
macos-app python 3.8.9 CVE-2019-12900 9.8 critical
macos-app python 3.8.9 CVE-2021-29921 9.8 critical
macos-app python 3.9.13 CVE-2015-20107 10.0 critical
npm cryptiles 2.0.5 CVE-2018-1000620 9.8 critical
npm extend 3.0.0 CVE-2018-16492 9.8 critical
npm handlebars 3.0.3 CVE-2021-23369 9.8 critical
npm handlebars 3.0.3 CVE-2021-23383 9.8 critical
npm jsonpointer 2.0.0 CVE-2021-23807 9.8 critical
npm lodash 3.10.1 CVE-2019-10744 9.1 critical
npm minimist 0.0.10 CVE-2021-44906 9.8 critical
npm minimist 0.0.8 CVE-2021-44906 9.8 critical
npm nodemailer 1.8.0 CVE-2020-7769 9.8 critical
npm redis 2.8.0 CVE-2015-4335 10.0 critical
npm redis 2.8.0 CVE-2018-11218 9.8 critical
npm redis 2.8.0 CVE-2018-11219 9.8 critical
npm xmlhttprequest-ssl 1.5.5 CVE-2021-31597 9.4 critical
python jmespath 1.0.1 CVE-2022-32511 9.8 critical The EC2 Mac AMI Scan output shows the list of all critical vulnerabilities in data volume introduced as part of this project.
For detailed information, refer to the documentation and sign up for a trial of the world’s first security vulnerability scanner for EC2 Mac AMIs to give it a spin. It takes less than five minutes to set it up and start vulnerability scanning EC2 Mac AMIs.
Please share your feedback with us on our slack. We are very excited to be able to bring innovative technology solutions for Mac Dev-Sec-Ops.