Up until a few years ago, the focus of software security was securing the perimeter. However, with the wide adoption of containers and service-based architecture for software applications and services, the responsibility of security is falling on developers. Securing the software supply chain is now the key area of focus with President Biden signing an executive order mandating changes on how software is secured during the development, build and deploy cycles for software companies that do business with the federal government.
Securing the software supply chain means knowing exactly what components are being used in the software products as it goes through the coding, building, testing, and deployment stages. This includes having visibility into even the code you didn’t write, like open-source or third-party dependencies, or any other artifacts, and being able to prove their provenance.
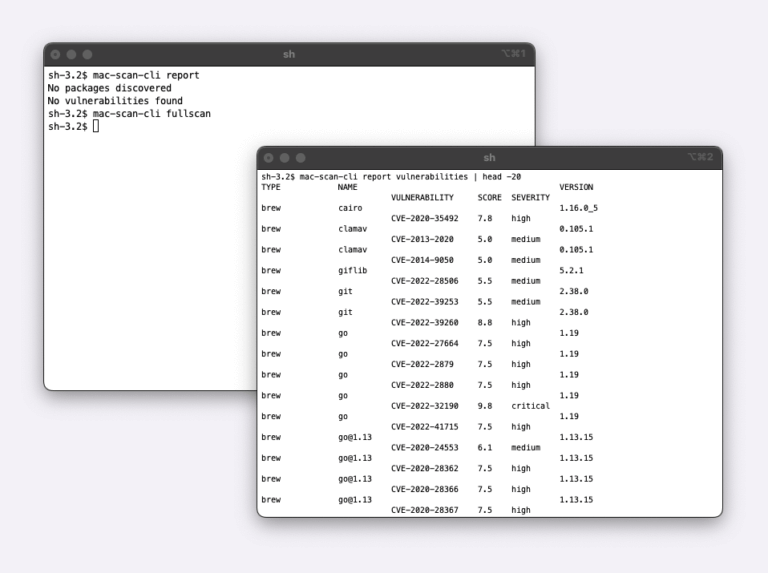
In the iOS and macOS application development, we see a limited set of solutions to enable software supply chain security. There are tools to do scanning of code repositories, App Store verification and that’s pretty much it. As the iOS apps move from the coding stage to the build and test stages, there is a large blind spot into what dependencies and packages get installed, downloaded during the subsequent build and test stage, and what if any vulnerabilities are introduced from those. Hence, here at Veertu, we have started to focus on building solutions specifically targeting these areas. This is why we’re happy to announce our first iteration: A security scanner that identifies all packages, dependencies, and associated vulnerabilities inside macOS Anka virtual machine images stored in the Anka registry. This enables you to identify and take corrective action on the images before you start using them in your CI/CD/automation pipelines. This is a critical step in ensuring that the macOS VM images that are used to build and test iOS applications don’t contain malicious packages and provide 100% visibility into packages installed and vulnerabilities inside those packages.
Today, we are announcing the early availability of this solution. Send us an email at [email protected] to participate in this beta program to start to test this in your Anka Build environment.