In the last few weeks, we have received a lot of inbound questions on the existence of T2 chip in new Apple Mac hardware models and how it impacts the ability to run macOS VMs. In this blog series, we will try to share our knowledge and insights on this topic.
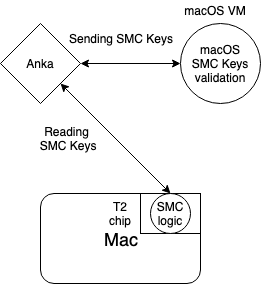
The focus of this first blog is on the role SMC plays in booting macOS and how T2 chip impacts this function. Apple T2 chip can control many aspects of the macOS platform over a single unified bus. One of them is, performing additional firmware validation in a trusted execution environment before supplying it to the chipset for execution. During macOS booting, macOS is accessing the hardware SMC chip to read key validation of the Mac.
In T2 enabled Mac hardware, T2 chip is acting as gatekeeper to SMC. Hackintosh and KVM based projects, which use Clover, are using the saved key of the SMC key, and bypassing the SMC validation. And, tools like ESXi access to SMC in this hardware is blocked by T2, unable to boot macOS VMs (https://twitter.com/lamw/status/1120368830427959297).
However, any solution that leverages macOS native hypervisor.framework like Anka, can boot macOS VMs without any issues. In this scenario, SMC calls are placed through the hypervisor.framework APIs and T2 is able to pass those onwards.
T2 chip in new Mac hardware not only acts as a gatekeeper during the boot process, but also prevents unauthorized access to internal SSD and Thunderbolt ports. So, even if any tool somehow manages to boot macOS VMs(using saved SMCkeys), it will not have access to the SSD. The workaround would be to use USB or network attached storage which is slow, not scalable and unreliable. More on this in our next blog.
Let us know if you have additional questions/comments in our slack channel.
References – https://www.apple.com/mac/docs/Apple_T2_Security_Chip_Overview.pdf
T2 in new Mac hardware and its impact on virtualizing and running macOS – Role of SMC
Share this post

In the dynamic world of software development, a streamlined Continuous Integration (CI) pipeline is the backbone of enterprises delivering reliable and efficient products. For macOS environments, the challenges of setting up and maintaining automation...

We’re starting a new annual tradition here at Veertu with our A Year of Anka blog posts. We want our customers to know how the product has grown over the past year and think this is a great avenue to do so. Please enjoy and happy holidays from all...

It has been several years since we made our first side by side comparison between Anka and Orka. A lot has changed, and we believe it’s important to make sure the information out there is accurate. We’ll be specifically addressing a newer...

Large and complex enterprises using Anka have many different demands, and we have worked to continue to develop innovative technology to meet these demands. Enterprise infrastructure hardware is often on the cutting edge, and they need advanced capabilities...

Veertu’s Anka and the new Anka Cloud Gitlab Executor Veertu’s Anka is a suite of software tools built on the macOS virtualization platform. It enables the execution of single or multi-use macOS virtual machines (VMs) in a manner similar to Docker....

It’s common that an organization’s macOS build system will download thousands, sometimes tens of thousands of third-party dependencies every hour. When building and testing iOS applications, it typically downloads and installs third-party...
Starting in Anka 3.1 we announced that Anka is now able to fully automate the macOS installation processes, disabling SIP, and enabling VNC — all previously manual steps users had to perform inside o the VM. At the time of writing this article,...

Starting in Anka 3.2, we’ve introduced a solution for scripting macOS UI user actions. You may ask, “Why would I want to do that?”. Well, often macOS configuration and applications do not have a CLI allowing you to perform certain actions...
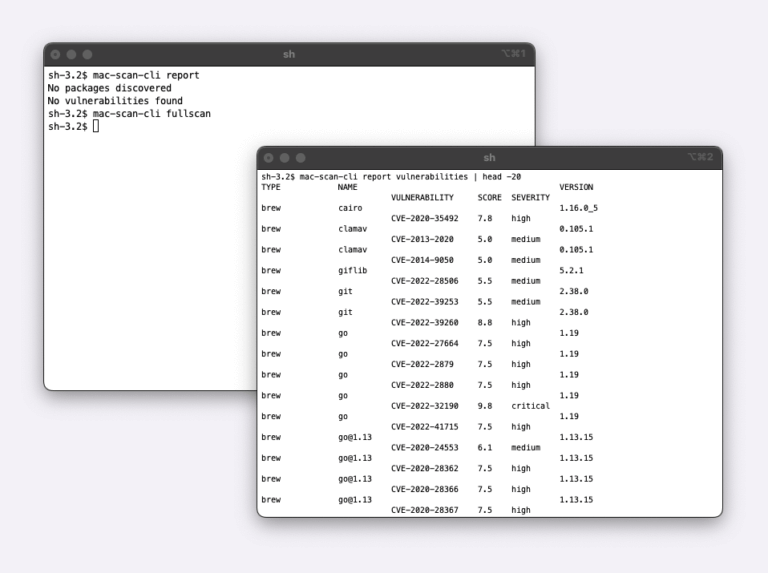
Today, we are announcing the Beta availability of the Mac Scan solution. Mac Scan software runs on macOS systems (bare metal, virtual, EC2 Mac) and scans downloads in real time for security vulnerabilities. There are multiple scenarios why you would...
